How malware started a Bitcoin hack that YouTube just can’t keep up with
We caught up with three architects who’s channels were paralyzed during a recent YouTube hack.
If you’ve been keeping up with tech news this week, you’ve likely heard about, or visualized first-hand, how several YouTube channels have submitted to a widespread cyberattack. Over the course of the last week or so, many paths have had their security accommodation by attacks, who have taken to broadcasting fake live streams advertising Bitcoin scams. In countless directions, the two attacks repetition a recent infringement on Twitter which engendered thousands of dollars in scammed Bitcoin after a Twitter employee was paid off to give intruders access.
Whilst the details of the spoofs themselves diversify somewhat, one core theme remains. All of them feel altogether let down by YouTube.
Yet the YouTube saga is very different from the recent Twitter breach in a number of ways, most significantly in YouTube’s seemingly slipshod response to the problem. We caught up with three major YouTube builders to identify areas exactly what happened to their directs, and what happened when they went to YouTube for help. Whilst the details of the hackers themselves diversify slightly, one core theme remains. All of them feel wholly let down by YouTube.
I spoke with Craig Groshek, superintendent/ owned of Chilling Entertainment, and the executive of Chilling Tales for Dark Night, an audio cruelty amusement direct of more than 1,500 videos and 340 k subscribers, about what happened.
Not merely was Craig a victim of the hack, but he has also been vocal on Twitter in trying to get help for many of the other founders who have been caught up in the gossip. Two such channels are ‘itsAamir’, and ‘PapaFearRaiser’. Between the two of them, they have roughly two million readers. Like Groshek, Aamir, and Jordan( PapaFearRaiser) Antle both had their directs endangered, and they extremely kindly is necessary to share their stories.
What happened?
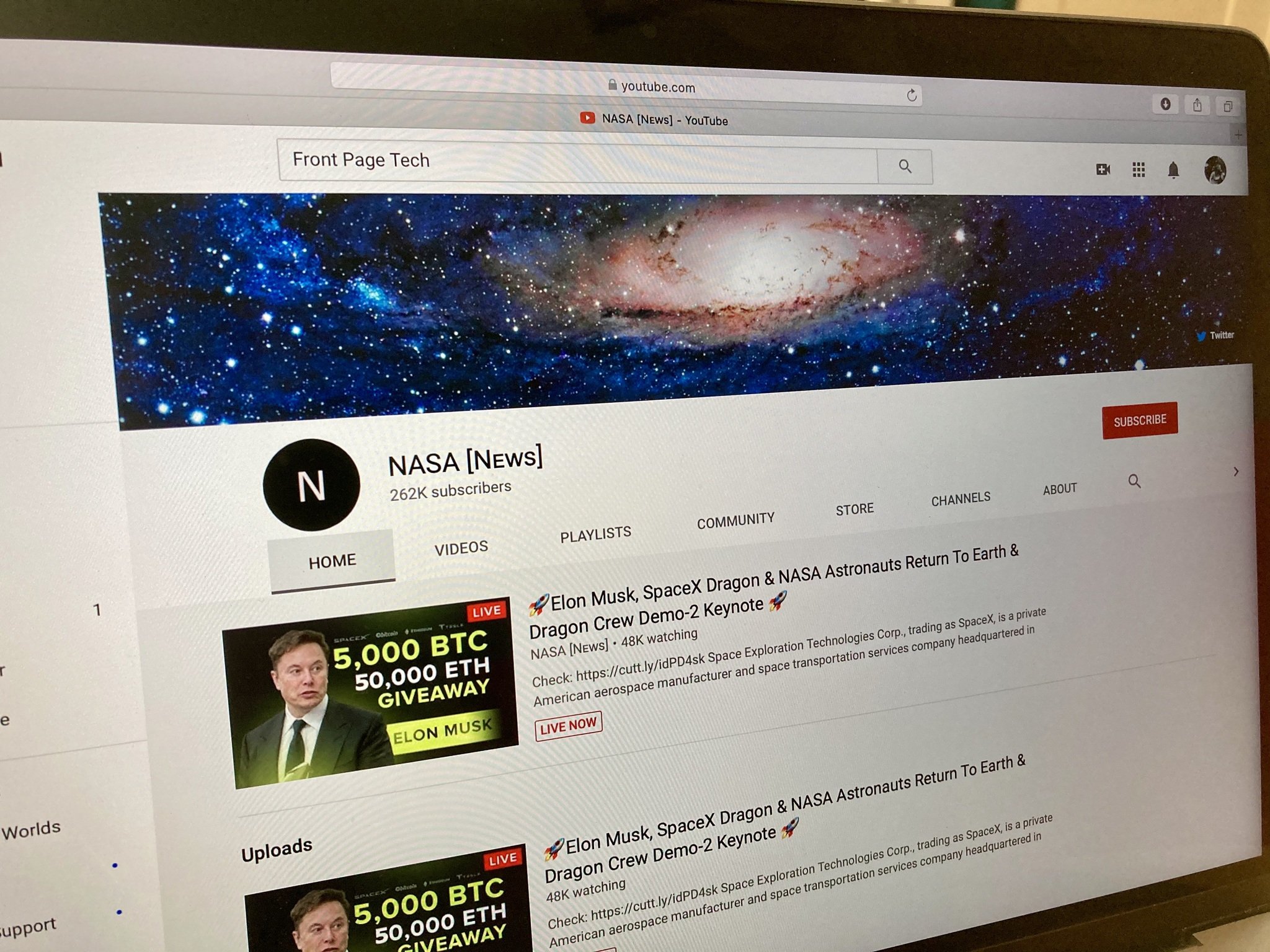
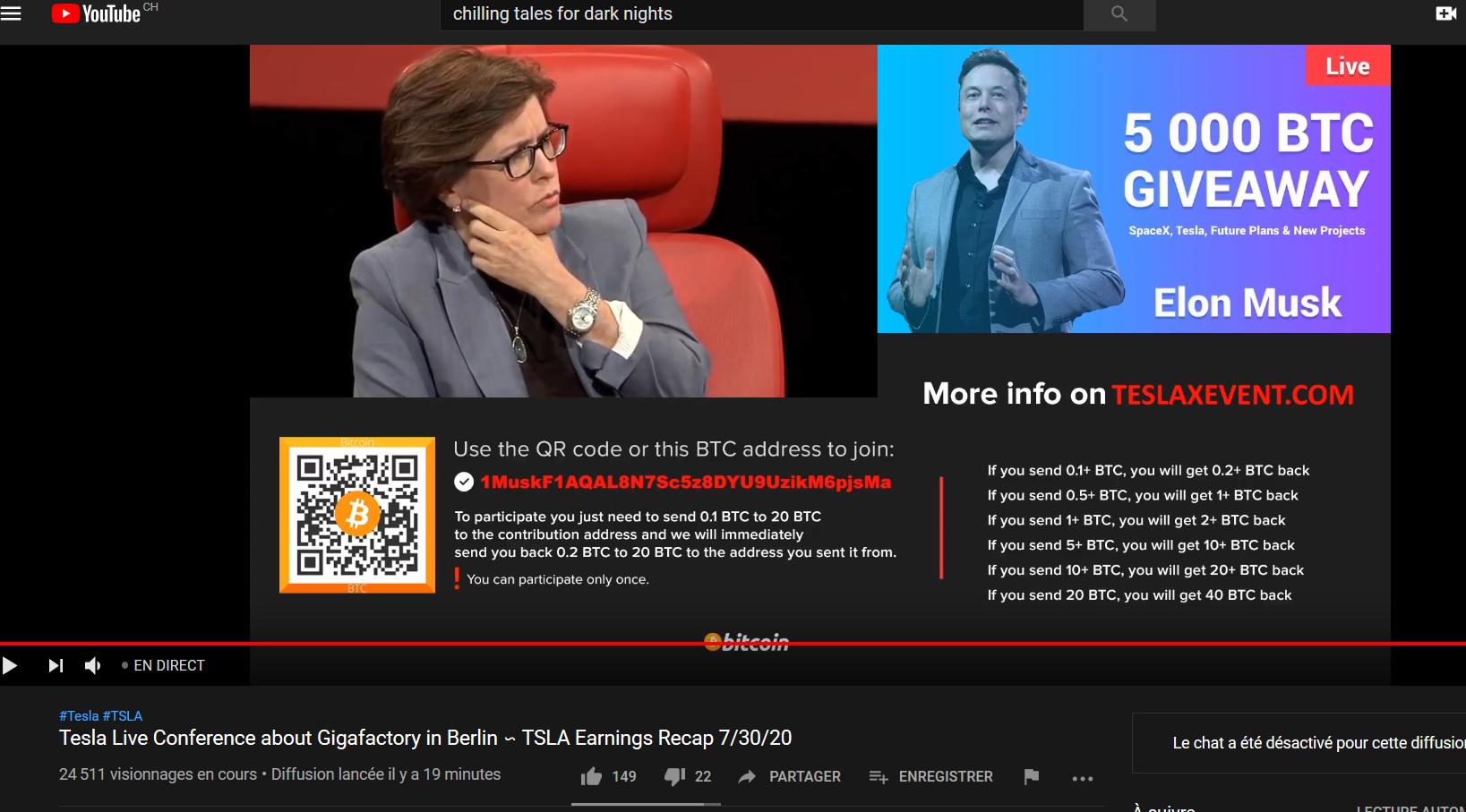
Aamir, Antle, and Groshek all have found that their YouTube accounts had been compromised over the course of the last couple of weeks. All three directs were considered to be broadcasting live Bitcoin scam videos promoting users to send in Bitcoin to a BTC address with the promise the money would be doubled. The videos was like the below epitome. All three also found that most, if not all of their YouTube videos had been made private, and their directs had been rebranded. This was common across all of the hackers we’ve seen on YouTube.
“My channel was jeopardized on July 29, 2020, at around 4 PM CT, ” says Groshek. “Hijackers wholly bypassed 2FA and did not change my passwords, or attempt to redirect my AdSense. Rather, they prepare all my videos to private except in cases of three, and put up Bitcoin scams live, and changed my name to Tesla, as well as my logo. They removed all my playlists and path communications, and drained my channel description.”
Many were quick to cry SIM swapping and some kind of 2FA bypass as some of these hackers unfolded. Nonetheless, the histories of all three of our builders now reveal a far more sinister mode of operation. In the run-up to their channels being compromised, Aamir, Antle, and Groshek all received emails from business, purportedly offering them sponsorship considers to push software on their channels.
“Two weeks ago, I got a sponsor email, where I was told to advertise “Resolve 16 ” video editor on my direct, ” interprets Aamir. Turns out, the email was imitation. After speaking first over mail, and then WhatsApp, Aamir was given a download link to the software. Lured in by the apparently sincere running, Aamir tried to run the software on his PC, only to be met with an error message, then good-for-nothing. At this extent, he knew something was amiss.
Antle( PapaFearRaiser) tells a same tale 😛 TAGEND
I virtually received what appeared to be a “professional” business email. This was person saying they represented a company called Magix Studios and we’re offering me a business opportunity to promote their produce. Once I agreed they transport me over the concoction link to download( which I premised would be safe as I’ve done this sort of thing before and it was 100% legit) and formerly I downloaded the WinRAR file and opened it up , nothing had happened.
Like Aamir, Antle knew something wasn’t right about the software he’d only sounded on. Within 60 instants, his part YouTube channel had been compromised.
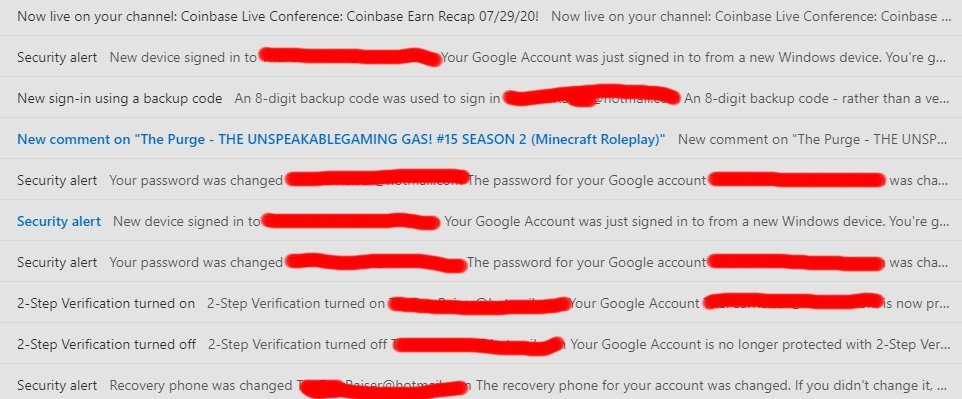
Jordan received a chilling chain of emails be said that the recuperation telephone had been changed for his direct, then to say that 2FA was to turn, then back on again, then that his password had been changed and a brand-new device had logged in. A backup system was used to sign into the channel, and then another brand-new manoeuvre alerting came through. Ultimately, he got an email to say that a video designation ‘Coinbase Live Conference: Coinbase Earn Recap 07/29/ 20 was now live on his path. All within the space of one hour.
Like Groshek and Aamir, all of Antle’s videos were prepared private, and the path was rebranded as Coinbase Live.
Definitely malware
“Definitely malware”. I caught up with Rich Mogull, Security Analyst for Securosis, and CISO for DisruptOps to dissect these narratives. “WinRAR files are one of the most common sources” he continues, explaining how intruders could use malware to create bonds from a trusted computer to modify password and security fixeds( including MFA or 2FA) to take control of an chronicle. When you switch off 2FA on Google, you don’t get a 2FA prompting to approve the modify, because you’ve previously logged in as a relied customer on a trusted machine or browser.
Further suggesting malware , not SIM swapping, was to blame, one of the first senses Antle received was to say his 2FA had been switched off , not that it had been used to sign in to a different manoeuvre or browser. The storeys don’t preclude some sort of 2FA, SIM swapping onrush( and there are plenty of other accommodation architects who might have fallen foul of this ), but they do seem to suggest that in these two cases, a malware attack was the primary make. Windows Defender told Aamir after the fact that the program he had downloaded seemed suspicious, but by then it was too late.
Windows Defender told Aamir after the fact that the program he had downloaded seemed suspicious, but by then it was too late.
Groshek’s story is a bit different. Like Aamir and Antle, he got a questionable email regarding a software sponsorship deal, but after offsetting further inquiries and receiving a software download relate, decided not to click on it. He did however notice a screenshot attached to the email. Mogull says this could indicate a “drive-by” malware attack, whereby malware could’ve been used even without Groshek clicking on the software download tie-up. Mogull further notes that sometimes in the case of a ‘drive-by’, you don’t even have to read the email.
YouTubers are no strangers to going sponsorship volunteers by emails, and Antle tells me he’s received them before, both real and fake, viewing possible deals for patrons. The forged emails are a common strand in every single story here, and even though Groshek didn’t click on his, it seems likely that getting the follow-up email in the first place might have been enough. There is certainly a chance that the malware, during the course of removing data from victim’s computers could’ve also picked up phone numbers for a SIM swap, and 2FA by way of SMS remains a moderately shaky space to shore up any online account. But malware seem to have the prime method used to compromise all three directs of the creators we spoke with.
Dropping the bullet
If the course these reports seem to have been compromised wasn’t harrowing enough, YouTube’s response was arguably worse.
Aamir tweeted YouTube the night he realized he’d been hacked, and received a DM from TeamYouTube. As with other developers, he was asked to fill out a special form, after which they said someone from the Creator Support Hacking Team would get in touch via email.
If the highway these details seem to have been compromised wasn’t harrowing fairly, YouTube’s response was arguably worse.
From Aamir’s understanding, YouTube has to generate the flesh and send a spoofed designer a special link, after which they have 72 hours to crowd it in, only the letter that said “We’ve caused you access to this form” contained no such tie. As of Thursday, August 6, Aamir had been waiting three days for YouTube to get in touch, after which YouTube simply told him that “the initial process to confirm an chronicle is spoofed can take a few weeks” and that they would be in touch. At the time of preparation of, Aamir’s channel is still totally compromised. He is still waiting for a response, his channel videos are all still private, and the directs identified is still branded ‘Ethereum Foundation[ LIVE] ‘.
Antle tells a same floor. “YouTube was also very painful, ” he says. “They mostly caused deadbeat responses and I was left in the dark for a majority of those 4 dates. Their Twitter team did not help much at all and attained me feel like my place wasn’t serious where reference is obviously was. They really didn’t make me feel like they had my security in mind.”
Thankfully for Antle, person from YouTube did in fact get back in touch, and his canal has principally been rehabilitated. But he still can’t publish videos hitherto, more on that later…
Groshek extremely got his channel back, but not without a fight. He told me how YouTube plies “little to no resources to explain how to contact them and get this resolved online”, with no mention of Twitter details like @TeamYouTube or Google Support forums. “They don’t tell you that TeamYouTube are middlemen with no authority”, he says, “or that these hackers and hijackings have been going on for years.”
Groshek says that his religion in YouTube is so shaken that he plans to leave the platform within the next year.
Groshek says it made a few weeks before anyone from YouTube Creator Support reached out via email, possibly after he posted on Google’s Support gatherings. You can imagine his amaze when he was told that they had no connection with @TeamYouTube and that he would have to provide all of the information to a second department again. Not simply that, but neither department could treat their own problems directly, and had a duty to forward the information on to their hijacking team. Groshek described his experience as “abysmal”, and that YouTube’s handling of the crisis had done more damage to him and the other paths than the intruders. He continues 😛 TAGEND
“Regardless of whether channel motorists “fell for” sophisticated phishing criticizes, etc, YouTube needs to recognize they are a primary target for these kinds of onrushes, and implement stronger methods of protection to prevent this from happening … They themselves acknowledge it’s happening very often they can’t keep up.
Groshek says that his sect in YouTube is so shaken that he plans to leave the platform within the next year.
But there’s more
It isn’t time YouTube’s direct interaction with the creators that is questionable. Several times the coming week, I and other YouTube customers have met bullshit Bitcoin live brooks propagandized to our YouTube homepages as recommended videos. You certainly couldn’t make it up.
YouTube is also recommending the stream to me. pic.twitter.com/ 7baqhOrKAo
— Rene Ritchie (@ reneritchie) August 6, 2020
The aftermath for all the creators, extremely Aamir( who still doesn’t have his channel back) is extensive. Many creators have lost customers as a result of the spoofs, 1,200 for Groshek, and more than 10,000 for Antle. Not to mention the loss in ad receipt whilst their directs were accommodation, both from videos that were hidden and from not given the opportunity to upload.
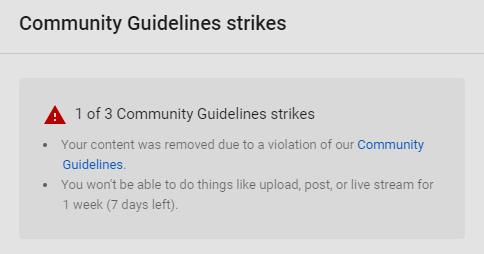
To add more insult to injury, both Antle and Groshek received Community Violation impresses on their paths due to the Bitcoin scam live streams.
To add more insult to harm, both Antle and Groshek received Community Violation disturbs on their directs due to the Bitcoin scam live flows. Despite presumably being aware of the spoof, YouTube rejected the appeal of both automatically. In a Tweet, Antle said 😛 TAGEND
Hey @ytcreators I literally requested this impres and just like I figured, it came rejected. Can you please do some internal team to help me? This really isn’t fair. I’m being rewarded for getting hacked? pic.twitter.com/ AQSlc2CIOu
— PapaFear VA [?] (@ TheFearRaiser) August 7, 2020
To add revile to the slander, YouTube then reset the upload injunction penalty on Antle’s channel because he had appealed the finding. He pled with simply four eras of the seven-day ban left, but he now has to wait a further seven days before he can upload any videos to his primary channel, the first of which will be a warning to his subscribers and the community about his experience.
Like Antle, Groshek was unable to post any videos on his Chilling Tales direct until yesterday, August 7. Way to go, YouTube.
Aamir, Antle, and Groshek are not the only designers was influenced by this. Notably, Apple leaker Jon Prosser had his YouTube channel FrontPageTech endangered. To stop any further damage, the entire FPT channel was removed from YouTube, 3 days later; they’ve heard nothing in response.
To recap
The three builders we spoke to are just the tip of the iceberg. As we has already mentioned, Groshek in particular has vocally criticized YouTube in its handled in dozens of channels who have been spoofed in recent periods, showing that plenty of other makes have been affected.
Add @AdamDuffArt and @jon_prosser to the list of those hacked by Bitcoin scammers the coming week. @ctfdn_official, @TheFearRaiser, @AlexHalford, @RecDTRH, @eltito_delfifa, @aamiristhis,& @KhujLeeFamily. How many more need to fall before you do something to stop this, @TeamYouTube? pic.twitter.com/ GJY4rTj 6ip
— Chilling Tales for Dark Nighttime (@ ctfdn_official) August 6, 2020
Given the specific characteristics of the hackers( the Bitcoin live rivers, privatizing videos, converting channel reputations) it seems highly likely that many of these attacks come from the same source. As indicated, all three pioneers we spoke to seem to have been exposed to malware through the promise of software sponsorship treats. Even though merely two of the three makes actually downloaded suspicious files, the probability of a ‘drive-by’ attack through the email Groshek received seems to suggest that malware, rather than SIM swapping may have been the primary procedure of attack.
It is impossible to say what happened in the many other bags regarding such channels with whom we haven’t spoken to, and there is all possibility that many different methods, or perhaps a combination of certain manipulates have been used to gain access to these accounts.
The three developers we spoke to are just the tip of the iceberg.
What doesn’t seem to be in any incredulity, however, was just the way inadequately YouTube seems to have gave the creators we spoke to. For them and countless others, YouTube is their source of income and livelihood. Yet, when they went to YouTube for help, good or perhaps no communication, direct affects for community misdemeanours, and spurned entreaties against those strikes have left a bitter taste. For Groshek, it was enough to convince him that it was time to leave the platform, it may well convince others.
At the time of writing, Google had not responded to our request for comment on this story.
Read more: androidcentral.com
 August 14, 2020
August 14, 2020